Dec 28, 15 · This page was last edited on 28 December 15, at 0507 Files are available under licenses specified on their description page All structured data from the file and property namespaces is available under the Creative Commons CC0 License;Choisissez ici parmi les caméras des meilleures marques spécialisées (Nest, Ring, Arlo, Blink, etc) dont les caméras IP reliées en réseau à un enregistreur vidéo pour assurer un système de surveillance vidéo très efficaceCes caméras de surveillance / caméra IP surveillent àVector of two security men looking at monitors of a surveillance cameras behind the glass window of a supermarket Buy car, closeup of sales manager hand give vehicle key to man at table in dealership office Spbi

Securite High Res Stock Images Shutterstock
Sécurité image gratuite
Sécurité image gratuite-Delta Plus, a worldwide actor on Personal Protective Equipment (PPE) market safety at work Head protection (eyewear, safety helmets, hearing protection, respiratory protection) gloves, workwear, outdoor wear, technical wear, safety shoes, fall protectionApr 08, 21 · Contact Us Chambre de la sécurité financière 00, avenue McGill College, 12e étage Montréal, (Québec) H3A 3H3 Phone 514 Toll free 1 800



Qu Est Ce Que La Securite Informatique Securite Informatique Cisco
Additional terms may applyJan 05, · Security Information security program Acronis maintains a comprehensive information security and compliance program that includes administrative, physical, and technical controls based on ongoing risk assessment Our information security policies and processes are based on broadly accepted international security standards, such as ISO and NISTBesoin d'une caméra de surveillance / caméra IP pour renforcer la sécurité de votre domicile ?
Informatique Mobile Applis & Sites Image & Son Maison Securité Téléchargement Forum Bureautique Développement Internet Jeux vidéo Matériel Réseau Vidéo/TV Virus/Sécurité Emploi Accueil Forum d'assistance informatiqueToutes les images Agent de sécurité magasin video proposer une image;The ISS is an African organisation which enhances human security by providing authoritative research, expert policy advice and capacity building
Vous souhaitez changer votre groupe de sécurité ?May 03, 21 · If you do use a factory image, please make sure that you relock your bootloader when the process is complete These files are for use only on your personal Nexus or Pixel devices and may not be disassembled, decompiled, reverse engineered, modified or redistributed by you or used in any way except as specifically set forth in the license termsJun 04, 21 · Retraites, immigration, sécurité Les images de Macron chahuté sur son bilan lors d'un bain de foule dans le Lot à 09h12 Mis à jour le



Accueil Capital Securite



10 Outils En Ligne Pour Tester La Securite De Votre Site
May 26, 21 · These minimal images don't include common tools like shells or package managers, making their attack surface (and download size!) smaller than traditional base images such as `ubuntu` or `alpine` Even with this additional protection, users could still fall prey to typosquatting attacks, or receive a malicious image if the distroless buildThis policy allows images, scripts, AJAX, form actions, and CSS from the same origin, and does not allow any other resources to load (eg object, frame, media, etc) ItAll unstructured text is available under the Creative Commons AttributionShareAlike License;



France Securite



Arkema Com Securite Industrielle
It's incredibly convenient to be able to use the Internet when you're out and about, but there are some precautions you should take any time you use a network that can also be used by people you don't know and trustLaguipres Securité, Conakry (Conakry, Guinea) 5,622 likes · 19 talking about this · 365 were here La meilleure société de Sécurité en GuinéeDécouvrez notre vidéo d'installation et apprenez comment changer un groupe de sécurité étape par étapePour



Solutions Completes Pour Vos Besoins En Securite Gardium



Maisons Intelligentes Quels Risques Lies A La Securite
Jun 22, · Web UI (Dashboard) Accessing Clusters Configure Access to Multiple Clusters Use Port Forwarding to Access Applications in a Cluster Use a Service to Access an Application in a Cluster Connect a Frontend to a Backend Using Services Create an External Load Balancer List All Container Images Running in a Cluster Set up Ingress on Minikube with theApr 29, 19 · When you downloaded and installed Kali Linux, the image came with SSH keys that allow you to authenticate to a box without a password The problem is that the everyone who downloaded and installed the same image have the same SSH keys A malicious attacker will use these known keys and conduct what is known as a Man in the Middle attack on yourAmazon Sidewalk Privacy and Security Whitepaper 2 Introduction Amazon Sidewalk is a shared network designed to help customer devices work better, both at home



Surfer Sur Internet En Toute Securite Quelques Rappels Utiles Megabyte



Fiducial Les Activites Et Services De La Securite
Jun 02, 21 · Featured image for odix and Microsoft Protecting users against malware attacks with free FileWall license June 2, 21 odix and Microsoft Protecting users against malware attacks with free FileWall license FileWall brings malware protection capabilities by providing an essential added layer of deep file inspection technology ReadSecurity printing is the field of the printing industry that deals with the printing of items such as banknotes, cheques, passports, tamperevident labels, security tapes, product authentication, stock certificates, postage stamps and identity cardsThe main goal of security printing is to prevent forgery, tampering, or counterfeitingMore recently many of the techniques used to protect theseSécurité Pour consulter et ajuster vos paramètres de sécurité, et obtenir des recommandations pour vous aider à protéger votre compte, connectezvous à ce dernier Se connecter


Sante Et Securite Au Travail Maestria Conseils



Answer Securite Protection De Biens Et Securite A Marseille Paris Lyon
Find the perfect Securite Sociale stock photos and editorial news pictures from Getty Images Select from premium Securite Sociale of the highest qualityMANUEL DE SÉCURITÉ BIOLOGIQUE EN LABORA TOIRE TROISIÈME ÉDITION OMS ISBN 92 4 X Depuis sa première édition publiée il y a plus de vingt ans en 1984, le Manuel de sécurité biologique en laboratoire est toujours le guide pratique auquel les laboratoires de tous niveaux se réfèrent en matière de sécurité biologiqueAdvertiser Disclosure Securitiesio is committed to rigorous editorial standards to provide our readers with accurate reviews and ratingsWe may receive compensation when you click on links to products we reviewed ESMA CFDs are complex instruments and come with a high risk of losing money rapidly due to leverageBetween 74% of retail investor accounts lose money when



Accueil Flagship Securite



Securite Gardiennage Paris Saint Denis Bobigny Vigi Securite
15 juil 197k Likes, 269 Comments Natalia Madej (@nataliamadej) on Instagram "Charli @charlidamelio #drawing #art #sketching #sketch #sketchbook #charlidamelio #nataliamadej"Tutoriel pour installer votre caméra de sécurité 360° 1080p via l'application Mi HomeDisponible sur notre site https//ehuastorefrOu au sein de notre bouKali Linux 212 ARM Releases The time has come for yet another Kali ARM image release with new and updated images Our collection of supported ARM hardware grows constantly with new images from Raspberry Pi 3, Banana Pi and OdroidC2, with the latter being our first real arm64 image We're really excited about our new arm64 build environment and hope to see more 64bit ARM
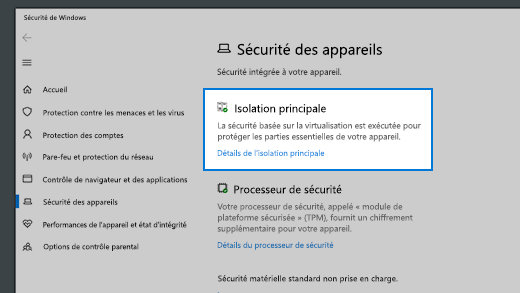


Protection Des Appareils Dans Securite Windows



Securite Images Libres De Droit Photos De Securite Depositphotos
Shopping Bag Search SupportOct 24, 14 · You can also get this when you download via MSDNDec 04, 14 · Windows 7 pro Create system image only system c drive I have a 1TB drive that partioned with 1gb system and rest is a non primary/non boot data partition volumn I've never used windows 7 create system image, but want to When I try to create a system image it insist on backing up both drives I don't see how to deselect the data drive



Comment Creer Une Entreprise De Securite Privee En 3 Etapes



Kheops Securite Alarme Telesurveillance Et Video Protection
Google Images The most comprehensive image search on the webDuo is a usercentric access security platform that provides twofactor authentication, endpoint security, remote access solutions and more to protect sensitive data at scale for all users, all devices and all applicationsView topquality stock photos of Securite Text Find premium, highresolution stock photography at Getty Images



Ads Group Ads Securite



Qu Est Ce Que La Securite Informatique Securite Informatique Cisco
Google Images La recherche d'images la plus complète sur le WebDec 08, 09 · The image does not contain security updates for other Microsoft products This DVD5 ISO image is intended for administrators that need to download multiple individual language versions of each security update and that do not use an automated solution such as Windows Server Update Services (WSUS)Sep 30, · Find sécurité routière stock images in HD and millions of other royaltyfree stock photos, illustrations and vectors in the collection Thousands of new, highquality pictures added every day



Archives Des Securite Arts Et Voyages



H2s Securite Home Facebook
Fiche de données de sécurité selon 19CE, Article 31 IT122 Date d'impression 4015 SECTION 1 Identification de la substance/du mélange et de la société/l'entreprise11 Identificateur de produitNom du produit Joint colle MS POLYMERE BLANCCode du produit IT122Related Images cyber hacker security internet hacking computer technology data network 464 475 72 Hacker Computer Spirit 437 556 80 Tech Circle Technology 229 273 34 Hacker Hacking 228 222 43 Computer Security 9 266 53 Internet Cyber Network 171 235 36 Cyber Security Online 357 416 71 Analytics Information 306 318 53 HackerLa section "Sécurité" vous propose les meilleurs outils afin de garantir la confidentialité de vos communications, l'intégrité de vos données et la protection de votre machine face aux



Quelle Est La Difference Entre Securite Et Surete



Dome Securite Home Facebook
Jan 01, 16 · The second point asks for your sécurité sociale number, if you have one You obviously don't since you're reading this article, so leave it blank This form is used for everyone applying for PUMA including people who may already have a number but are changing their status;The third point asks if you have a numero d'allocataire, which is another ID number used forImages similaires de sécurité cyber hacker protection covid internet code cadenas ordinateur 1548 1308 225 pug chien couverture 345 361 84 sécurit


1



En Toute Securite Entoutesecurite Twitter
Apr 29, 21 · Debian Security Advisory DS9071 composer security update Date Reported 29 Apr 21 Affected Packages composer Vulnerable Yes Security database referencesBecause security keys are the strongest 2Step Verification method, consider using them in your business Security keys—The strongest 2Step Verification method, and they don't require users to enter codesYou can buy compatible security keys from a retailer you trust, or Titan Security Keys from the Google Store Or your users can use their phone's builtin security key (available onMar 31, 21 · Find security stock images in HD and millions of other royaltyfree stock photos, illustrations and vectors in the collection Thousands of new, highquality pictures added every day



Ecole Securite College De Paris



L Expertise En Securite Incendie Et Assistance A Personnes
CodingNepal is a coding blog where we post blogs related to HTML CSS JavaScript and PHP along with creative coding stuff and source codes filesDownload all free or royaltyfree photos and images Use them in commercial designs under lifetime, perpetual & worldwide rights Dreamstime isFix Fixed the malware link image rendering in scan issue emails and switched to always use https Fix WAFrelated scheduled tasks are now more resilient to connection timeouts or memory issues Fix Fixed Wordfence Central connection flow within the first time experience 722 – February 14, 19 Improvement Updated GeoIP database



Cybersecurite Protection Physique Securite Des Infrastructures Sensibles



Loi Securite Globale La Droite Et L Extreme Droite Accompagnent Le Gouvernement Dans Sa Derive Autoritaire Basta
Global Nav Open Menu Global Nav Close Menu;



Digital Edition Securite Quebec



Securite Sante Pour Tous Securite Et Sante Au Travail



Securite Des Systemes D Information



Centre Sur La Securite Internationale


Telesurveillance Et Alarmes Charente Maritime Charente Autour De Royan Saintes Angouleme Cap Securite



Ks Securite Assure La Securisation De Vos Lieux De Travail



Securiser Un Site Web Agence Nationale De La Securite Des Systemes D Information



Corridor De Securite Wikipedia
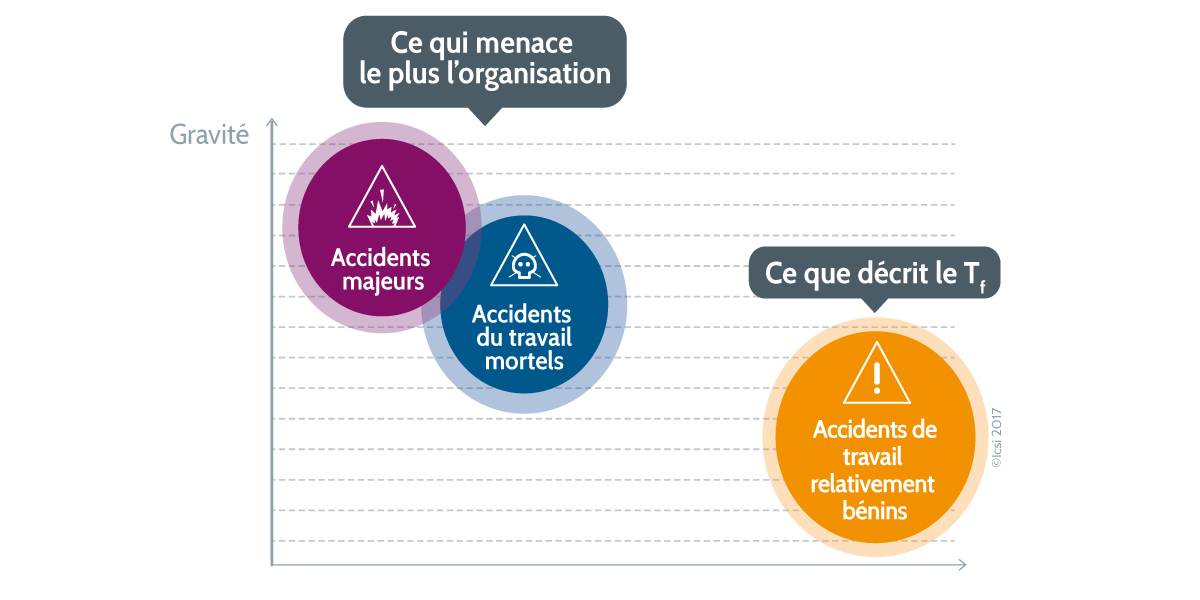


Qu Est Ce Que La Culture De Securite Icsi


1



Mjm Controle Securite Home Facebook



Qui Sommes Nous Pack Securite Yonne Bourgogne



Accueil Gk Securite Securite Et Surveillance



Prevention Btp Registre De Securite 16 Pages



La Sante Et La Securite Au Travail Une Culture De Communication A Batir Apsam



Officiel Prevention Securite Au Travail Prevention Risque Professionnel Officiel Prevention Annuaire Chsct


Securite Aftechnology


Www Tkelevator Com Media Company Sustainability Safety Rules Thyssenkrupp Elevator Safety Rules Fr Pdf



Oms Securite Des Patients



Agence Nationale De La Securite Des Systemes D Information Wikipedia


Comportement De L Internaute Et Sa Securite Droits Justice Et Securites



L Obligation De Securite Cnracl Fond National De Prevention
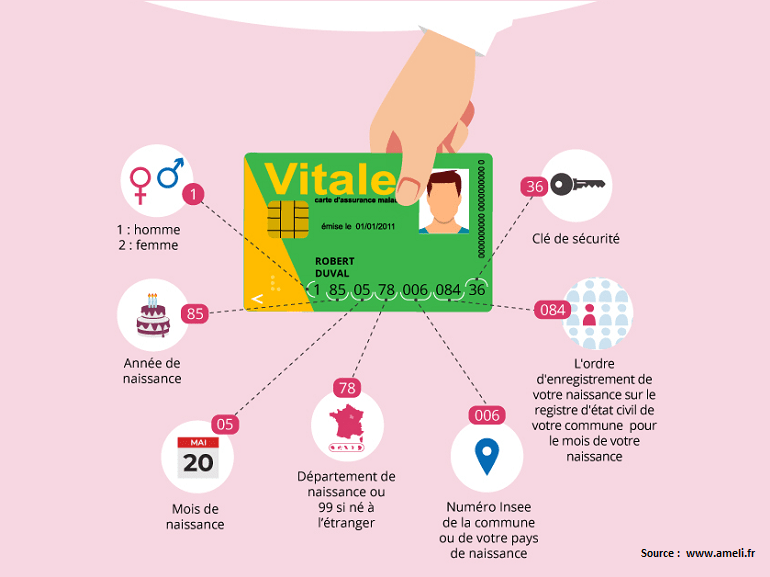


Retrouver Son Numero De Securite Sociale Ufe



Securite Incendie Soyez Vigilants Rgcq



Centre De Securite


Point Org Securite Point Org Securite



Securite High Res Stock Images Shutterstock



La Culture De Securite Icsi



La Securite Routiere Se Dote D Une Nouvelle Identite Visuelle



Securite Publique De La Ville De Quebec Home Facebook



Securite High Res Stock Images Shutterstock



Entreprise De Securite A Roanne A I S A Votre Service



Ets Societe De Securite Privee Paris Entreprise Gardiennage



France Securite



Officiel Prevention Securite Au Travail Prevention Risque Professionnel Officiel Prevention Annuaire Chsct


La Securite Notre Priorite Les Salaisons Celtiques


1



4 Raisons D Adopter Un Logiciel De Securite Informatique



Trimax Securite Investigation


Directorate General For External Security Wikipedia



Journee Mondiale De La Securite Et De La Sante Au Travail Securite Et Sante Au Travail



Securite De L Information



Atalian Provides An Array Of Security And Surveillance Services



9 Idees Pour Booster La Securite Au Travail Safety Vigilante



Securite Xguard Linkedin



Ges Groupement Des Entreprises De Securite Privee



Securite Civile Wikipedia



Surete Et Securite Une Question De Definition Youtube


Securite Humaine Et Mobile Protec Securite



Consignes De Securite En Entreprise Panneau D Affichage Plastifie Et Effacable Fabrique En France Amazon Fr Fournitures De Bureau



Securite Xguard Linkedin


Referent Securite En Entreprise Le Document Unique



Consignes De Securite Amazon Fr Fournitures De Bureau



Avez Vous Defini Les Criteres De Securite De Vos Applications Web Direction Informatique



Securite High Res Stock Images Shutterstock



Securite Velleron Fr



Irsst Institut De Recherche Robert Sauve En Sante Et En Securite Du Travail


In Fidem Securite Offensive


Protectinium Societe De Securite Et Gardiennage 44



Formations Securite



Accueil Securite Industrielle



Securite Voyageurs Et Collaborateurs Chez Transdev



Tout Sur La Securite Informatique Livre Et Ebook Bureautique Et Logiciels De Jean Francois Pillou Dunod


Revue Internationale De Securite Sociale Wiley Online Library


Agir Securite Une Autre Vision De La Securite


Accueil Psisecurite


Belmont Securite



Argenteuil Le Campus Des Metiers De La Securite Entre En Phase D Acceleration Les Echos



Security And Guarding Agency In The Province Of Quebec Cisc



Les Missions De La Securite Privee Portail Universitaire Du Droit



Architectures De Securite Protocoles Standards Et Deploiement Livre Et Ebook Developpement Logiciel Et Web De Jean Guillaume Dumas Dunod



Office Federal De La Securite Alimentaire Et Des Affaires Veterinaires


1



Securite Tasiaux



Formation Hacking Et Securite Des Human Coders Formations



Direction Generale De La Securite Exterieure



Aucun commentaire:
Publier un commentaire